| |
APPENDIX B: TECHNOLOGY MARKETS BACKGROUND |
| 1 |
Big Data HLS and Internal Security Market |
| 1.1 |
Market & Technology Background |
| 1.2 |
Big Data Security |
| 1.2.1 |
Access and Delivery Infrastructure |
| 1.2.2 |
Data Centric Access Control |
| 1.2.3 |
Access Control |
| 1.2.4 |
Access Control in Databases |
| 1.2.5 |
Encryption Prescribed Access Control |
| 1.2.6 |
Trusted Bootstrapping |
| 1.2.7 |
Big Data Security Analytics |
| 1.3 |
Big Data: HLS and Internal Security Applications |
| 1.4 |
Big Data Security Industry: SWOT Analysis |
| 1.4.1 |
Strengths |
| 1.4.2 |
Weaknesses |
| 1.4.3 |
Opportunities |
| 1.4.4 |
Threats |
| 1.5 |
Big Data Security Market Drivers |
| 1.6 |
Big Data Security Market Inhibitors |
| 2 |
Bio-Agents & Infectious Disease Detection Homeland Security & Public Safety Market |
| 2.1 |
Market Background |
| 2.2 |
Bio-Detection Technologies |
| 2.2.1 |
Sampling the Environment |
| 2.2.2 |
Bio-Detectors in a Multitude of Ambient Settings |
| 2.2.3 |
Bio-Detection Triggering |
| 2.2.4 |
Sample Collection |
| 2.2.5 |
Bio-Particle Detectors |
| 2.2.6 |
Bio-Agent Identification |
| 2.2.7 |
National Biosurveillance Systems |
| 2.3 |
Bio-Agents & Infectious Disease Detection: Homeland Security & Public Safety Applications |
| 2.4 |
Bio-Agents & Infectious Disease Detection: Business Opportunities & Challenges |
| 2.5 |
Bio-Agents & Infectious Disease Detection Homeland Security & Public Safety Industry: SWOT Analysis |
| 2.5.1 |
Strengths |
| 2.5.2 |
Weaknesses |
| 2.5.3 |
Opportunities |
| 2.5.4 |
Threats |
| 2.6 |
Bio-Agents & Infectious Disease Detection Market Drivers |
| 2.7 |
Bio-Agents & Infectious Disease Detection Market Inhibitors |
| 3 |
Biometrics Homeland Security & Public Safety Market |
| 3.1 |
Biometric Market & Technology background |
| 3.2 |
Multimodal Biometric Systems |
| 3.3 |
Homeland Security & Perimeter Security Applications |
| 3.4 |
Biometrics: Business Opportunities & Challenges |
| 3.5 |
Biometrics Homeland Security & Public Safety Industry: SWOT Analysis |
| 3.5.1 |
Strengths |
| 3.5.2 |
Weaknesses |
| 3.5.3 |
Opportunities |
| 3.5.4 |
Threats |
| 3.6 |
Biometrics Market Drivers |
| 3.7 |
Biometrics Market Inhibitors |
| 4 |
C2/C4ISR Systems HLS & Public Safety Market |
| 4.1 |
Market & Technology Background |
| 4.2 |
C2/C4ISR Systems: Business Opportunities |
| 4.3 |
C2/C4ISR Systems HLS & Public Safety Industry: SWOT Analysis |
| 4.3.1 |
Strengths |
| 4.3.2 |
Weaknesses |
| 4.3.3 |
Opportunities |
| 4.3.4 |
Threats |
| 4.4 |
C2/C4ISR Systems Market Drivers |
| 4.5 |
C2/C4ISR Systems Market Inhibitors |
| 5 |
Chemical, Hazmat & Nuclear Detection HLS & Public Safety Market |
| 5.1 |
Technology Background |
| 5.1.1 |
Chemical Agent Detection technologies |
| 5.1.2 |
Nuclear/Radiological Detection Technologies |
| 5.1.2.1 |
The Advanced Spectroscopic Portal (ASP) |
| 5.1.2.2 |
Human Portable Radiation Detection Systems (HPRDS) Program |
| 5.1.2.3 |
Nuclear- Radiological People Screening Portals |
| 5.2 |
Market Background |
| 5.2.1 |
Chemical Plant Security |
| 5.2.2 |
Nuclear/Radiological Detection Markets |
| 5.3 |
Chemical, Hazmat & Nuclear Detection: Business Opportunities & Challenges |
| 5.4 |
Chemical, Hazmat & Nuclear Detection HLS & Public Safety Industry: SWOT Analysis |
| 5.4.1 |
Strengths |
| 5.4.2 |
Weaknesses |
| 5.4.3 |
Opportunities |
| 5.4.4 |
Threats |
| 5.5 |
Chemical, Hazmat & Nuclear Detection Market Drivers |
| 5.6 |
Chemical, Hazmat & Nuclear Detection Market Inhibitors |
| 6 |
Cloud Based Security HLS & Public Safety Market |
| 6.1 |
HLS and Public Security Cloud computing and Security |
| 6.2 |
Cloud Security Threats |
| 6.3 |
Cloud security |
| 6.4 |
Cloud Security Industry: SWOT Analysis |
| 6.4.1 |
Strengths |
| 6.4.2 |
Weaknesses |
| 6.4.3 |
Opportunities |
| 6.4.4 |
Threats |
| 6.5 |
Cloud Security Market Drivers |
| 6.6 |
Cloud Security Market Inhibitors |
| 7 |
Communication Systems & Devices HLS & Public Safety Market |
| 7.1 |
Market & Technology Background |
| 7.1.1 |
Market Background |
| 7.1.2 |
Emergency Communication: Technology Background |
| 7.2 |
HLS & Public Safety Communication Equipment Market: Business Opportunities |
| 7.2.1 |
Managed Services for Shared/Core Services |
| 7.2.2 |
Migration from “Simple” to “Integrated” Networks |
| 7.2.3 |
Communication Systems & Devices: Business Opportunities |
| 7.3 |
Communication Systems & Devices Market Drivers |
| 7.4 |
Communication Systems & Devices Market Inhibitors |
| 8 |
Counter-IED Technologies HLS & Public Safety Market |
| 8.1 |
Market & Technology Background |
| 8.2 |
Counter-IED Technologies: Business Opportunities & Challenges |
| 8.2.1 |
Maintenance and Upgrades (Particularly of Jammers, and Armored Trucks) |
| 8.2.2 |
Sensors and Other Electronic Systems Upgrade/s |
| 8.2.3 |
Standoff Suicide Bombers Detection |
| 8.2.4 |
Suicide Bombers Detonation Neutralization |
| 8.2.5 |
Standoff Detection of VBIED |
| 8.2.6 |
VBIED Detonation Neutralization |
| 8.2.7 |
Standoff Explosive Detection in Urban Environment |
| 8.2.8 |
Large Area IED Detection Coverage |
| 8.2.9 |
IED Placement Detection |
| 8.2.10 |
Active Armors for Vehicles |
| 8.3 |
Counter-IED Technologies HLS & Public Safety Industry: SWOT Analysis |
| 8.3.1 |
Strengths |
| 8.3.2 |
Weaknesses |
| 8.3.3 |
Opportunities |
| 8.3.4 |
Threats |
| 8.4 |
Counter-IED Technologies Market Drivers |
| 8.5 |
Counter-IED Technologies Market Inhibitors |
| 9 |
Cybersecurity HLS & Public Safety Market |
| 9.1 |
Cyber Terror & Crime Mitigation Market & Technology Background |
| 9.1.1 |
Cyber Terror & Crime |
| 9.1.2 |
Cyber Warfare |
| 9.1.3 |
Denial of Service |
| 9.1.4 |
Deliberate Manipulation of Information |
| 9.1.5 |
Detection of Unauthorized Activity |
| 9.1.6 |
Anti-Malware Cyber-Security |
| 9.1.7 |
Privacy Enhanced Technologies (PETs) |
| 9.2 |
Key Cyber Security Vendors |
| 9.3 |
Cybersecurity: Business Opportunities |
| 9.4 |
Cybersecurity HLS & Public Safety Industry: SWOT Analysis |
| 9.4.1 |
Strengths |
| 9.4.2 |
Weaknesses |
| 9.4.3 |
Opportunities |
| 9.4.4 |
Threats |
| 9.5 |
Cybersecurity Market Drivers |
| 9.6 |
Cybersecurity Market Inhibitors |
| 10 |
Decontamination of CBRN & Hazmat Incidents HLS & Public Safety Market |
| 10.1 |
CBRN & Hazmat Decontamination Technology Background |
| 10.1.1 |
Decontamination of CBRN & Hazmat incidents |
| 10.1.2 |
Decontamination Core Technologies |
| 10.1.3 |
The Decontamination Cycle |
| 10.2 |
Decontamination Strategy |
| 10.3 |
CBRN & Hazmat Decontamination Market Background |
| 10.4 |
The Decontamination Industry |
| 10.5 |
Decontamination of CBRN & Hazmat Incidents Market Drivers |
| 10.6 |
Decontamination of CBRN & Hazmat Incidents Market Inhibitors |
| 11 |
Electronic Fencing HLS & Public Safety Market |
| 11.1 |
Electronic Fences Technologies |
| 11.1.1 |
Vibration Sensors Mounted on Fence |
| 11.1.2 |
Capacitance Sensors Fence |
| 11.1.3 |
Strain Sensitive Cables Fence |
| 11.1.4 |
Fiber Optic Fence |
| 11.1.5 |
Taut Wire Fence |
| 11.1.6 |
Ported Coax Buried Line Fence |
| 11.1.7 |
Buried Geophone Fence |
| 11.2 |
Electronic Fencing: Business Opportunities & Challenges |
| 11.3 |
Electronic Fencing HLS & Public Safety Industry: SWOT Analysis |
| 11.3.1 |
Strengths |
| 11.3.2 |
Weaknesses |
| 11.3.3 |
Opportunities |
| 11.3.4 |
Threats |
| 11.4 |
Electronic Fencing Market Drivers |
| 11.5 |
Electronic Fencing Market Inhibitors |
| 12 |
Explosives Trace Detection (ETD) HLS & Public Safety Market |
| 12.1 |
Market & Technology Background |
| 12.1.1 |
ETD Technologies |
| 12.1.2 |
ETD Market Background |
| 12.2 |
Explosives Trace Detection (ETD): HLS & Public Safety Applications |
| 12.2.1 |
Explosives Detected by Explosives Trace Detection |
| 12.2.2 |
Explosives Trace Detection Configuration |
| 12.2.3 |
ETD Applications |
| 12.3 |
Explosives Trace Detection (ETD): Business Opportunities & Challenges |
| 12.4 |
Explosives Trace Detection (ETD) HLS & Public Safety Industry: SWOT Analysis |
| 12.4.1 |
Strengths |
| 12.4.2 |
Weaknesses |
| 12.4.3 |
Opportunities |
| 12.4.4 |
Threats |
| 12.5 |
Explosives Trace Detection (ETD) Market Drivers |
| 12.6 |
Explosives Trace Detection (ETD) Market Inhibitors |
| 13 |
Intrusion Detection Systems HLS & Public Safety Market |
| 13.1 |
Market & Technology Background |
| 13.1.1 |
Passive Infrared (PIR) Motion Detection |
| 13.1.2 |
Access Control Systems |
| 13.2 |
Intrusion Detection Systems: Business Opportunities & Challenges |
| 13.2.1 |
Challenges |
| 13.2.2 |
Business Opportunities |
| 13.3 |
Intrusion Detection Systems HLS & Public Safety Industry: SWOT Analysis |
| 13.3.1 |
Strengths |
| 13.3.2 |
Weaknesses |
| 13.3.3 |
Opportunities |
| 13.3.4 |
Threats |
| 13.4 |
Intrusion Detection Systems Market Drivers |
| 13.5 |
Intrusion Detection Systems Market Inhibitors |
| 14 |
Mass Emergency Notification HLS & Public Safety Market |
| 14.1 |
Mass Emergency Notification Technology Background |
| 14.1.1 |
Introduction |
| 14.1.2 |
Text Alert Systems |
| 14.1.3 |
Voice Alert Systems |
| 14.1.4 |
Siren Systems |
| 14.1.5 |
The U.S. Emergency Alert System (EAS) |
| 14.1.6 |
Cell broadcast Mass Emergency Notification |
| 14.2 |
Mass Emergency Notification: HLS & Public Safety Applications |
| 14.3 |
Mass Emergency Notification: Business Opportunities & Challenges |
| 14.4 |
Mass Emergency Notification HLS & Public Safety Industry: SWOT Analysis |
| 14.4.1 |
Strengths |
| 14.4.2 |
Weaknesses |
| 14.4.3 |
Opportunities |
| 14.4.4 |
Threats |
| 14.5 |
Mass Emergency Notification Market Drivers |
| 14.6 |
Mass Emergency Notification Market Inhibitors |
| 15 |
Metal Detectors HLS & Public Safety Market |
| 15.1 |
Market & Technology Background |
| 15.1.1 |
Hand-Held Metal Detectors |
| 15.1.1.1 |
The Market |
| 15.1.1.2 |
Principles of Operation |
| 15.1.1.3 |
Technology & operational Essentials |
| 15.1.1.4 |
Hand-Held Metal Detectors – Technology Trends |
| 15.1.2 |
Metal Detection Portals |
| 15.1.2.1 |
The Market |
| 15.1.2.2 |
Metal Detection Portals Technology |
| 15.2 |
Metal Detectors: Business Opportunities & Challenges |
| 15.3 |
Metal Detectors HLS & Public Safety Industry: SWOT Analysis |
| 15.3.1 |
Strengths |
| 15.3.2 |
Weaknesses |
| 15.3.3 |
Opportunities |
| 15.3.4 |
Threats |
| 15.4 |
Metal Detectors Market Drivers |
| 15.5 |
Metal Detectors Market Inhibitors |
| 16 |
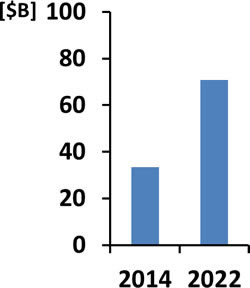
Natural & Manmade Disaster Early Warning, Rescue & Recovery Equipment Market – 2014-2022 |
| 16.1 |
Market & Technology Background |
| 16.2 |
Training and Education Markets |
| 16.3 |
Emergency Medical Services (EMS) |
| 16.4 |
Emergency Management Software |
| 16.5 |
Natural & Manmade Disaster Early Warning, Rescue & Recovery Equipment HLS & Public Safety Industry: SWOT Analysis |
| 16.5.1 |
Strengths |
| 16.5.2 |
Weaknesses |
| 16.5.3 |
Opportunities |
| 16.5.4 |
Threats |
| 16.6 |
Natural & Manmade Disaster Early Warning, Rescue & Recovery Equipment Market Drivers |
| 16.7 |
Natural & Manmade Disaster Early Warning, Rescue & Recovery Equipment Market Inhibitors |
| 17 |
Non-Lethal Weapons HLS & Public Safety Market |
| 17.1 |
Non-Lethal Weapons Technology Background |
| 17.2 |
Less-Lethal Weapons: Market Background |
| 17.3 |
Non-Lethal Weapons: HLS & Public Safety Applications |
| 17.4 |
Non-Lethal Weapons: Business Opportunities & Challenges |
| 17.5 |
Non-Lethal Weapons HLS & Public Safety Industry: SWOT Analysis |
| 17.5.1 |
Strengths |
| 17.5.2 |
Weaknesses |
| 17.5.3 |
Opportunities |
| 17.5.4 |
Threats |
| 17.6 |
Non-Lethal Weapons Market Drivers |
| 17.7 |
Non-Lethal Weapons Market Inhibitors |
| 18 |
Personal (Ballistic & CBRNE) Protective Gear HLS & Public Safety Market |
| 18.1 |
Market & Technology Background |
| 18.1.1 |
Personal Body Armor |
| 18.1.2 |
Respiratory Protective Equipment |
| 18.1.3 |
CBRN and Hazmat Personal Protective Gear |
| 18.2 |
Personal (Ballistic & CBRNE) Protective Gear HLS & Public Safety Industry: SWOT Analysis |
| 18.2.1 |
Strengths |
| 18.2.2 |
Weaknesses |
| 18.2.3 |
Opportunities |
| 18.2.4 |
Threats |
| 18.3 |
Personal (Ballistic & CBRNE) Protective Gear Market Drivers |
| 18.4 |
Personal (Ballistic & CBRNE) Protective Gear Market Inhibitors |
| 19 |
HLS and Public Security RFID Market – 2014-2022 |
| 19.1 |
HLS & Public RFID and RFID Security: Market Background |
| 19.1.1 |
RFID-based e-ID Personal Documents Markets |
| 19.1.2 |
RFID-Based Systems “Registered Traveler” Programs |
| 19.1.3 |
E-Passport Programs |
| 19.1.4 |
HLS and Public Safety RFID-Based Systems Supply Chain Markets |
| 19.2 |
HLS and Public SecurityRFID and RFID Security:Technology Background |
| 19.3 |
RFID Systems Security |
| 19.3.1 |
Tag Data Security |
| 19.3.2 |
Reader Security |
| 19.4 |
RFID Market Drivers |
| 19.5 |
RFID Market Inhibitors |
| 20 |
Standoff Explosives & Weapon Detection HLS and Public Security Market |
| 20.1 |
Market & Technology Background |
| 20.1.1 |
Suicide Bombers & Vehicle Borne IEDs |
| 20.2 |
Standoff Explosives & Weapon Detection: Business Opportunities & Challenges |
| 20.2.1 |
Business Opportunities |
| 20.2.2 |
PBIED & VBIED Detection: Technological Challenges |
| 20.3 |
Standoff Person-Borne and Vehicle-Borne Explosives & Weapon Detection SWOT Analysis |
| 20.4 |
Standoff Explosives & Weapon Detection: Market Drivers |
| 20.5 |
Standoff Explosives & Weapon Detection: Market Inhibitors |
| 21 |
Tomographic Explosive Detection Systems (EDS) Market |
| 21.1 |
Explosive Detection Systems: Technology Background |
| 21.1.1 |
Explosive Detection Systems: Throughput |
| 21.1.2 |
EDS Principle of Operation |
| 21.1.3 |
Hybrid Tomographic EDS & 2D X-Ray Screening |
| 21.1.4 |
EDS Certification |
| 21.1.5 |
EDS Throughput vs. Price |
| 21.1.6 |
Aviation Security: EDS Checked Luggage Screening |
| 21.2 |
Aviation Security: EDS Market Background |
| 21.3 |
Aviation Security Explosive Detection Systems (EDS) Industry: SWOT Analysis |
| 21.3.1 |
Strengths |
| 21.3.2 |
Weaknesses |
| 21.3.3 |
Opportunities |
| 21.3.4 |
Threats |
| 21.4 |
Tomographic Explosive Detection Systems (EDS) Market Drivers |
| 21.5 |
Tomographic Explosive Detection Systems (EDS) Market Inhibitors |
| 22 |
Vehicle & Container Screening Portals HLS & Public Safety Market |
| 22.1 |
Vehicle & Container Screening Portals Technologies |
| 22.1.1 |
Comparison of Container-Vehicle Screening Technologies |
| 22.1.2 |
X-Ray Container-Vehicle Screening Systems |
| 22.1.3 |
Dual Energy X-Ray Container-Vehicle Screening |
| 22.1.4 |
Dual-View X-Ray Container-vehicle Screening |
| 22.1.5 |
Backscatter X-Ray Container-vehicle Screening |
| 22.1.6 |
Gamma Ray Systems Container-vehicle Screening |
| 22.1.7 |
Linac Based X-Ray Container-vehicle Screening systems |
| 22.1.8 |
Neutron Activation Container-vehicle Screening Systems |
| 22.2 |
Vehicle & Container Screening Portals: Market Background |
| 22.3 |
Vehicle & Container Screening Portals Industry: SWOT Analysis |
| 22.3.1 |
Strengths |
| 22.3.2 |
Weaknesses |
| 22.3.3 |
Opportunities |
| 22.3.4 |
Threats |
| 22.4 |
Vehicle & Container Screening Portals: Market Drivers |
| 22.5 |
Vehicle & Container Screening Portals: Market Inhibitors |
| 23 |
Video Surveillance HLS & Public Safety Market |
| 23.1 |
Market & Technology Background |
| 23.2 |
Video Surveillance: HLS & Public Safety Applications |
| 23.3 |
Video Surveillance: Business Opportunities & Challenges |
| 23.4 |
Video Surveillance HLS & Public Safety Industry: SWOT Analysis |
| 23.4.1 |
Strengths |
| 23.4.2 |
Weaknesses |
| 23.4.3 |
Opportunities |
| 23.4.4 |
Threats |
| 23.5 |
Video Surveillance Market Drivers |
| 23.6 |
Video Surveillance Market Inhibitors |
| 24 |
Video Analytics HLS & Public Safety Market |
| 24.1 |
Market & Technology Background |
| 24.2 |
Video Analytics: HLS & Public Safety Applications |
| 24.3 |
Video Analytics: Business Opportunities |
| 24.4 |
Video Analytics HLS & Public Safety Industry: SWOT Analysis |
| 24.4.1 |
Strengths |
| 24.4.2 |
Weaknesses |
| 24.4.3 |
Opportunities |
| 24.4.4 |
Threats |
| 24.5 |
Video Analytics Market Drivers |
| 24.6 |
Video Analytics Market Inhibitors |
| 25 |
X-Ray Explosives Screening Market |
| 25.1 |
X-Ray Screening Technology Background |
| 25.1.1 |
2D X-Ray, EDS and ETD Explosives Detection Technologies – Pros and Cons |
| 25.1.2 |
X-Ray Systems – Characteristics |
| 25.1.3 |
X-Ray Systems – Principles of Operation |
| 25.1.4 |
People Screening Backscatter AIT |
| 25.2 |
X-Ray Screening Market Background |
| 25.3 |
X-Ray Screening: Business Opportunities & Challenges |
| 25.4 |
X-Ray Screening HLS & Public Safety Industry: SWOT Analysis |
| 25.4.1 |
Strengths |
| 25.4.2 |
Weaknesses |
| 25.4.3 |
Opportunities |
| 25.4.4 |
Threats |
| 25.5 |
X-Ray Screening Market Drivers |
| 25.6 |
X-Ray Security Systems Market: Inhibitors |
| |
METHODOLOGY, DISCLAIMER & COPYRIGHT |
| 26 |
The Report Research Methodology |
| 26.1 |
Report Structure |
| 26.2 |
Assumptions |
| 26.3 |
Research Methodology |
| 27 |
Disclaimer & Copyright |